What is Key Management Service? #
Why Encryption?
- Scenario: You are storing credit card details or personal data in a system. What if someone hacks the database? We need a way to protect sensitive information even if it gets stolen.
- Encryption: Converts data into unreadable format using keys – only someone with the right key can read it.
Symmetric Key Encryption
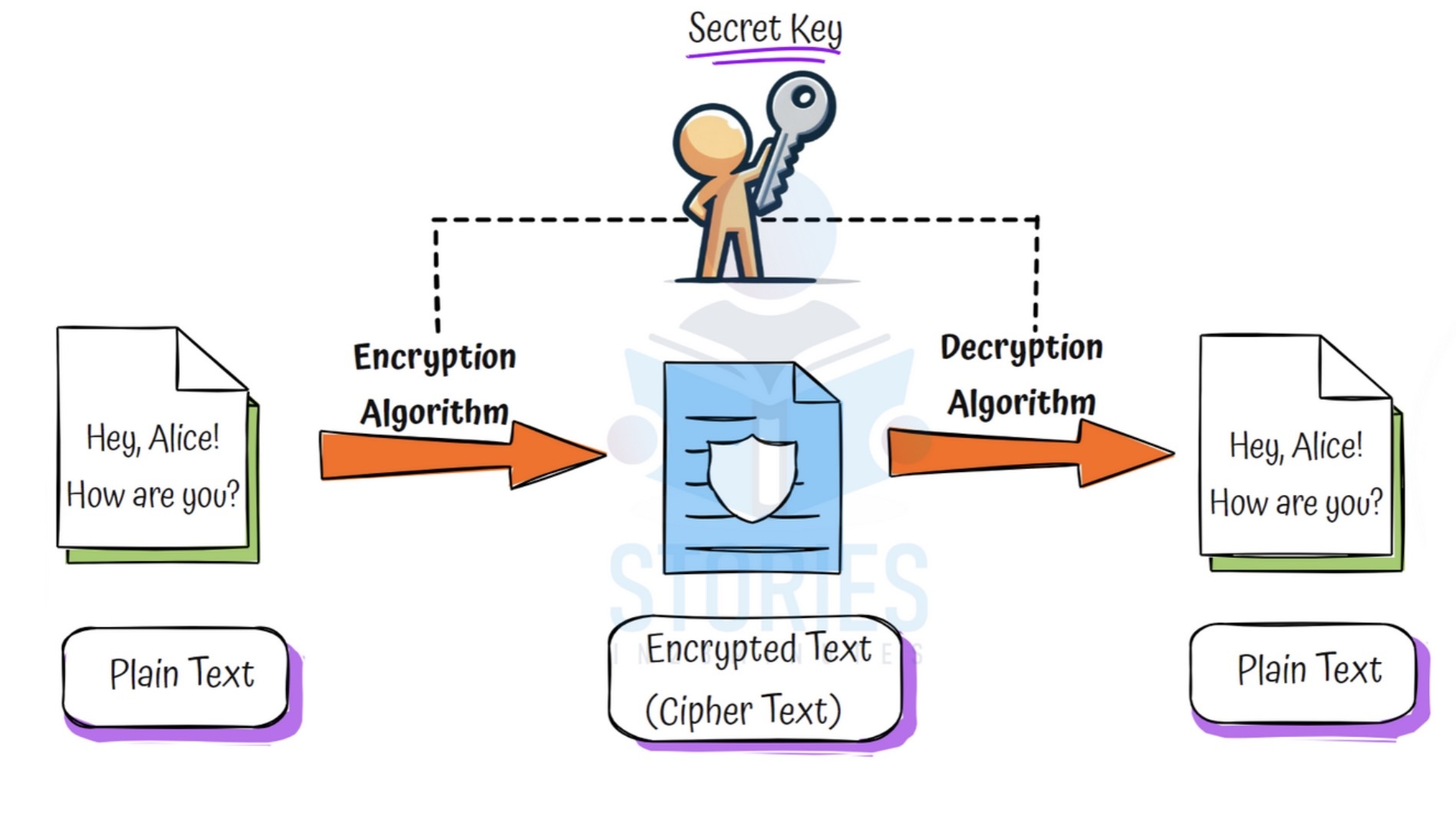
- One Key: Same key is used to encrypt and decrypt data
- Simple & Fast: Very efficient for encrypting large amounts of data
- Problem: Key must be shared with others securely – that’s risky!
Key Questions for Symmetric Encryption
- Which Algorithm?: Choose safe options like AES
- How to Protect Key?: Store securely (e.g., in Key Management Services)
- How to Share Key?: Avoid sending it directly – consider using asymmetric encryption to share it!
Asymmetric Key Encryption (Public Key Cryptography)
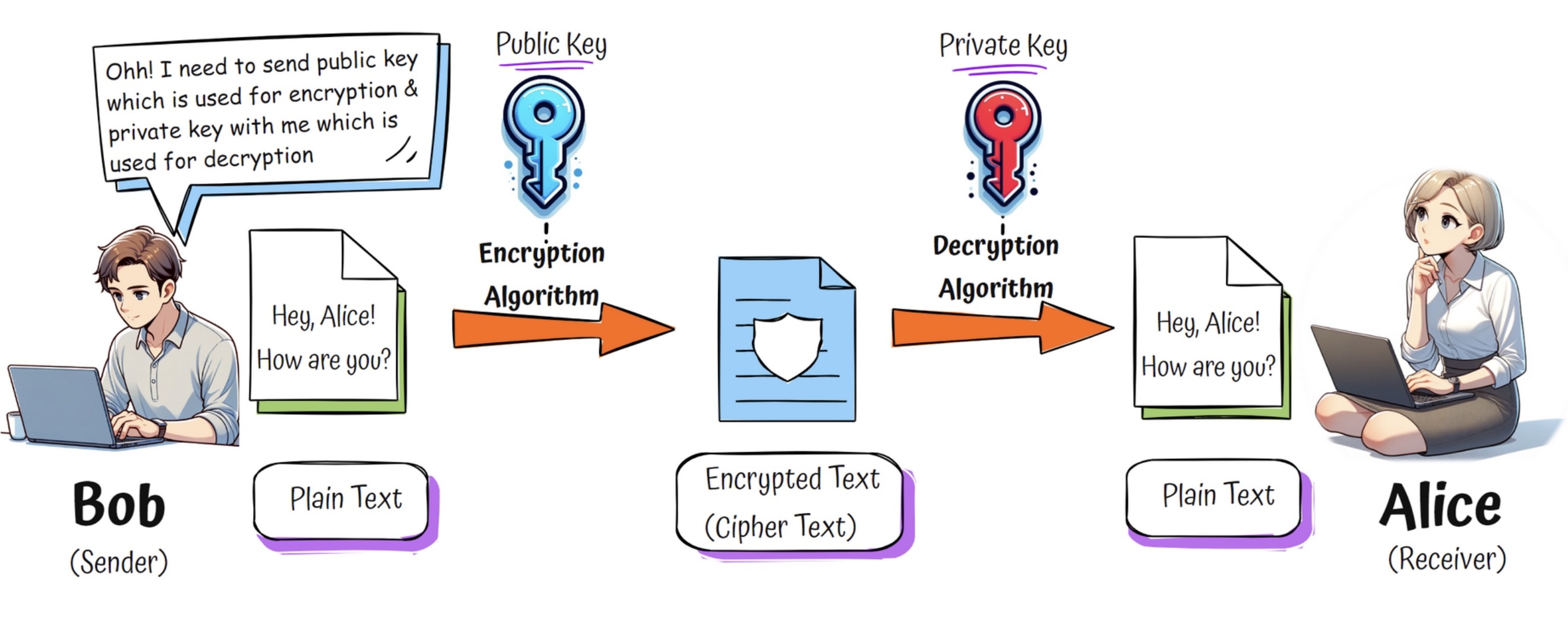
- Two Keys:
- Public Key: Shared with everyone
- Private Key: Kept secret
- Encryption Flow:
- Encrypt with Public Key
- Decrypt with Private Key
- Use Case: You can receive data securely from anyone without needing to share a key
Common Misconception
- Public Key ≠ Easy to Reverse: Math behind it (e.g., RSA) makes it nearly impossible to compute the private key from the public key
What is Key Management Service?
- Definition: A service that helps create, store, rotate, and manage encryption keys
- Goal: Keep your data secure — at rest and in transit — using strong encryption practices
Services That Typically Use Key Management Services
- Object Storage – Encrypt files and backups
- Block Storage – Protect disk volumes for VMs and databases
- Databases – Encrypt data at rest
- Messaging Services – Secure messages in queues or topics
- Secrets Management – Store and encrypt passwords, tokens, and API keys
- Backup & Disaster Recovery – Encrypt snapshots and backup data
- Logging & Monitoring – Encrypt logs stored in logging services
HSM (Hardware Security Module)
- Scenario: Imagine storing ultra-sensitive data like government records, banking transactions, or healthcare info. You want the encryption keys to be super secure — even cloud provider admins shouldn’t access them.
- What is HSM?: A physical device (available in the cloud too) that stores and manages encryption keys with strong protection.
- Highest Level of Security: HSMs offer FIPS 140-2 Level 3 compliance — trusted by banks, governments, and regulated industries.
- Dedicated and Isolated: In the cloud, HSMs are not shared. Only your organization has access to your HSM instance.
- Use Case: Needed when regulations require physical separation and dedicated control of key material.
- Cloud Examples: AWS CloudHSM, Azure Dedicated HSM, Google Cloud HSM.
Cloud Managed Services for Key Management and HSM
- AWS: AWS Key Management Service (KMS), AWS CloudHSM
- Azure: Azure Key Vault, Azure Dedicated HSM
- Google Cloud: Google Cloud Key Management Service (KMS), Google Cloud HSM
Encryption at Rest vs Encryption In Transit #
What is Encryption at Rest?
- Definition: Encrypts data when it's stored on disk – like in databases, storage, or backups
- Goal: Prevent unauthorized access if storage is compromised
- Use Cases: Object storage, block storage, database files, snapshots
- Managed By: Server-side encryption using KMS or HSM (in most cases)
What is Encryption in Transit?
- Definition: Encrypts data while it's being transmitted across networks
- Goal: Protect data from being read or modified while moving between users, apps, or services
- Use Cases: API calls, browser access, microservices
- How is it done?: Uses secure protocols like HTTPS and mTLS, powered by SSL/TLS certificates
- HTTPS: Commonly used for user-to-application communication — for example, when a user accesses a web app through a browser or an app calls an external API
- mTLS (Mutual TLS): Used for service-to-service communication within secure environments like microservices or internal APIs — both client and server authenticate each other using certificates for stronger trust and protection
1: What is the Role of SSL/TLS Certificates?
- Identity Verification: Confirms that the server you are connecting to is the real
example.com— not an imposter - Encryption Enablement: Helps establish a secure, encrypted connection between client and server using HTTPS
- Trust Establishment: Issued by trusted Certificate Authorities (CAs), making browsers trust the website
- Foundation of HTTPS: Without a valid SSL/TLS certificate, HTTPS cannot be established — the browser will warn users
- Used in Handshake: The certificate is shared during the handshake to initiate secure communication and exchange encryption keys securely
SSL vs TLS
- SSL (Secure Sockets Layer): The original encryption protocol for securing web traffic — now outdated and insecure
- TLS (Transport Layer Security): The modern, more secure version that replaced SSL
- Current Standard: TLS 1.2 and TLS 1.3 are widely used today; SSL is deprecated
- Naming Confusion: People still say “SSL certificate,” but TLS is what’s actually used
- Bottom Line: When you see HTTPS, it's powered by TLS, not SSL — even if the certificate is called an “SSL certificate”
2: How does HTTPS work?
- Step 01: A user opens a website by typing
https://example.comin the browser - Step 02: The browser contacts the server and requests a secure connection — this begins the TLS handshake
- Step 03: The server responds with its digital certificate (SSL/TLS certificate) issued by a trusted Certificate Authority (CA)
- Step 04: The browser verifies the certificate to confirm the server’s identity is valid and trusted
- Step 05: The browser and server negotiate encryption parameters and securely establish a session key using asymmetric encryption
- Step 06: Both the browser and server now use this session key to encrypt and decrypt all further communication
- Widely Used: To access websites securely through a browser
3: How does Mutual TLS(mTLS) work?
- Step 01: A client (typically another app) tries to connect to a secure server using HTTPS
- Step 02: The server sends its TLS certificate to the client to prove its identity
- Step 03: The client verifies the server’s certificate using a trusted Certificate Authority (CA)
- Step 04: Unlike standard HTTPS, the server now asks the client for its own certificate
- Step 05: The client sends its client certificate to the server
- Step 06: The server verifies the client's certificate to confirm the client’s identity
- Step 07: Once both sides are authenticated, they generate a shared session key for encrypted communication
- Step 08: All future data is encrypted and decrypted using the session key — both client and server are trusted
- Widely Used: In secure microservice communication
What are DDoS Attacks? #
What is a DDoS Attack?
- Scenario: Your website or service suddenly becomes slow or unavailable. It is not a bug — it is being overwhelmed by fake traffic.
- Goal of the Attacker: Make your service unusable by flooding it with more traffic than it can handle.
DDoS = Distributed Denial of Service
- Definition: A cyber attack where multiple machines send massive traffic to a server, app, or network
- Goal: Deny access to legitimate users by exhausting system resources
Impact of DDoS Attacks
- Downtime: Website or app becomes unreachable
- Revenue Loss: E-commerce and service platforms lose sales
- Reputation Damage: Users may lose trust
- Resource Waste: Servers and bandwidth consumed by fake traffic
DDoS Protection in the Cloud
1: Built-In Basic Protection in Many Cloud Services
| Service Type | Basic DDoS Protection Built-In? | Purpose |
|---|---|---|
| Cloud Load Balancers | Yes | Automatically protect backend services |
| DNS Services | Yes | Globally redundant DNS reduces DNS attacks |
| Content Delivery Networks (CDNs) | Yes | Absorb and filter traffic at edge locations |
2:Advanced DDoS Protection
- For mission-critical or high-risk workloads
- Includes:
- Real-time traffic monitoring
- 24/7 response support
- Examples:
- AWS: AWS Shield (Advanced)
- Azure: Azure DDoS Protection (Standard)
- Google Cloud: Cloud Armor (with Adaptive Protection)
What are CVEs? #
What are CVEs?
- Scenario: Imagine your app uses an open-source library, and suddenly a security team warns, "It has a CVE!" What does that mean?
- CVE: Stands for Common Vulnerabilities and Exposures — a system for identifying and cataloging publicly known security flaws.
- Definition: A unique ID assigned to a known security vulnerability
- Example:
CVE-2024-12345might refer to a serious flaw in a library your app uses - Managed by: The MITRE Corporation, in coordination with vendors and researchers
- Goal: Make it easy to communicate, track, and remediate vulnerabilities across systems
Why CVEs Matter in Cloud and DevOps
- Transparency: One global ID for each vulnerability — no confusion
- Automation: Security scanners use CVEs to detect flaws in your code or dependencies
- Patch Management: Helps you quickly know what needs to be updated
- Risk Awareness: CVE severity (via CVSS score) helps prioritize what to fix first
Example Flow
- A vulnerability is found in
log4j - It’s published as
CVE-2021-44228 - Security tools scan your cloud resources and alert you
- You patch or mitigate the vulnerability
Cloud Managed Services That Help Track CVEs
- AWS: AWS Inspector (automatic CVE scanning on EC2, Lambda, containers)
- Azure: Microsoft Defender for Cloud (vulnerability assessment)
- Google Cloud: Container Analysis (detects CVEs in images and VMs)
Where Does OWASP Fit in Cloud Application Security? #
Where Does OWASP Fit in Cloud Application Security?
- Scenario: You're building a web application and wondering which threats to prioritize. OWASP helps you focus on the most common and critical ones.
- OWASP: The Open Worldwide Application Security Project—an industry-recognized authority that publishes security best practices, especially the OWASP Top 10.
- Definition: OWASP provides a list of the most critical security risks for web applications
- Goal: Help teams build secure applications by addressing the most likely and most impactful vulnerabilities
Example OWASP 10 List (Changes with Time)
- Broken Access Control → Misconfigured IAM roles or API permissions
- Cryptographic Failures → Missing encryption at rest or in transit
- Injection → SQL/NoSQL injection through unvalidated user input
- Insecure Design → Missing security controls like throttling, logging, and input validation filters
- Security Misconfiguration → Public S3 buckets, open firewalls, exposed ports
- Vulnerable and Outdated Components → Old libraries in cloud-deployed containers
- Identification and Authentication Failures → Missing MFA or improper session handling
- Software and Data Integrity Failures → No verification of code
- Security Logging and Monitoring Failures → Logs not enabled or not monitored
- Server-Side Request Forgery (SSRF) → Attacker tricks the server into making requests to internal services (e.g., accessing internal IPs)
Why Application Firewall in Cloud? #
Why Application Firewall in Cloud?
- Scenario: Imagine your app is deployed in the cloud and starts receiving suspicious traffic — SQL injections, bots, DDoS attacks. You need a shield.
- Application Firewall: A protective layer that filters and monitors HTTP/S traffic to your cloud application.
What is a Cloud Application Firewall?
- Definition: A Web Application Firewall (WAF) that protects cloud apps by inspecting incoming requests and blocking malicious patterns
- Goal: Prevent common attacks (like those in OWASP Top 10) before they reach your app
- Deployment: Typically placed in front of APIs, web apps, and load balancers
Key Capabilities
- Threat Detection: Blocks SQL injection, cross-site scripting (XSS), CSRF, SSRF
- Traffic Filtering: Allow or deny requests based on IPs, headers, geolocation
- Rate Limiting: Control traffic spikes
- Bot Protection: Detect and block malicious bots or scrapers
- Logging & Alerting: Monitor threats and alert teams in real time
Best Practices
- Enable default OWASP protection rules
- Set up geo-blocking if your app is regional
- Use rate limiting for login and API endpoints
- Regularly review WAF logs and update rules
- Combine with CDN and DDoS protection for stronger defense
Cloud Managed Services for Application Firewall
- AWS: AWS WAF
- Azure:Azure Web Application Firewall
- Google Cloud: Cloud Armor
Why Shift Left Security? #
Why Shift Left Security?
- Scenario: Imagine discovering a security flaw just before production. Fixing it now delays release, increases cost, and risks customer trust.
- Shift Left Security: Catch and fix security issues early in the development process, rather than waiting until the end.
What is Shift Left Security?
- Definition: Practice of integrating security early in the software development lifecycle (SDLC)
- Goal: Detect vulnerabilities sooner, reduce cost and risk, and deliver secure code faster
- Mindset: Security is everyone’s responsibility, not just the security team’s job
Key Principles of Shift Left Security
- Early and Continuous: Security checks start during coding, not after deployment
- Integrated Tools: Use security tools inside CI/CD pipelines
- Developer Empowerment: Give developers tools and training to fix issues themselves
- Automation: Automate scans to avoid manual, late-stage bottlenecks
Common Shift Left Security Practices
- Static Application Security Testing (SAST)
- Analyze code for vulnerabilities during development
- Software Composition Analysis (SCA)
- Detect known CVEs in open-source dependencies
- Secrets Scanning
- Prevent hardcoded API keys, passwords, and tokens
- Container and IaC Scanning
- Secure Dockerfiles, Kubernetes configs, Terraform scripts
- Security Unit Tests
- Add tests for auth, input validation, and access control
Benefits of Shifting Security Left
- Faster Fixes: Easier to fix issues while code is still fresh
- Lower Costs: Cheaper to fix bugs early
- Improved Culture: Developers take ownership of security
- Fewer Late Surprises: Fewer last-minute release delays
| Cloud Provider | Service | Focus Area |
|---|---|---|
| AWS | Amazon Inspector | Scans EC2, Lambda, and container images for CVEs |
| Amazon ECR Image Scanning | Scans container images in Elastic Container Registry for vulnerabilities | |
| Azure | Microsoft Defender for Cloud | Performs vulnerability assessments for VMs, containers, and app services |
| Microsoft Defender for Containers | Detects CVEs in container images and Kubernetes clusters | |
| Google Cloud | Artifact Analysis | Scans container images and artifacts for known vulnerabilities (CVEs) |
| OS Configuration (OS Config) | Detects and reports OS-level vulnerabilities in VMs |