What is the purpose of Virtual Networks and Subnets in the Cloud? #
What is a Virtual Network in the Cloud?
- Scenario: You’re building a web application with a frontend, backend service, and a database — all hosted in the cloud. You want the frontend to talk to the backend, and the backend to talk to the database, but you don’t want that internal communication to go over the public internet.
- Goal: Create your own private network in the cloud to keep internal traffic secure and isolated, and control access to it.
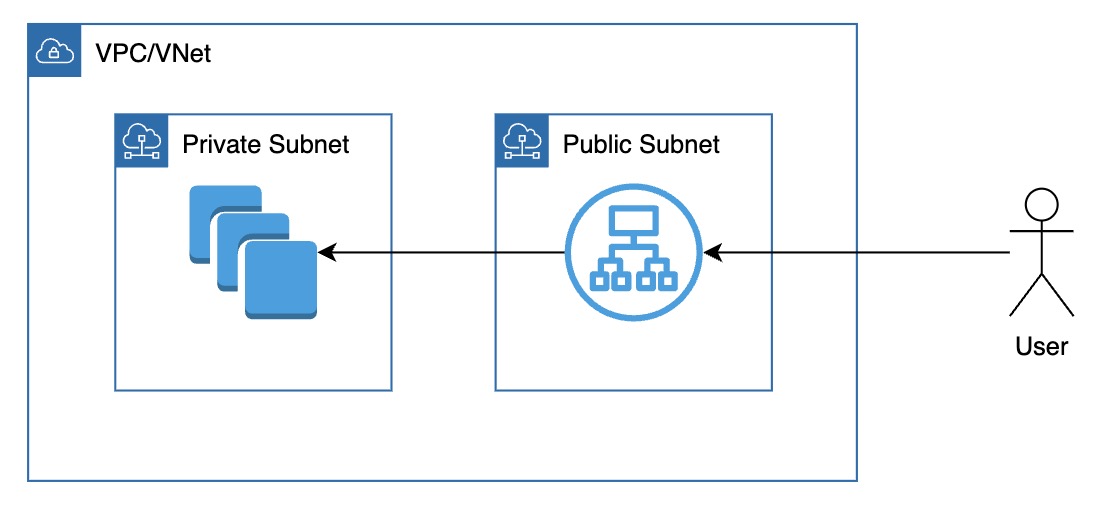
Virtual Network (VNet / VPC)
- Definition: An isolated, configurable network environment in the cloud
- Purpose: Connect and secure cloud resources (e.g., VMs, storage, databases)
- Key Features:
- Traffic Isolation: One virtual network is invisible to others
- Control Inbound/Outbound Traffic: Control traffic to and from the network
- Best Practice: Place all resources inside your virtual network

Why do we need Subnets?
- Challenge: Different resources in your virtual network have different access requirements
- Example:
- Load balancers need to be accessible from the internet
- Databases should stay private and only be accessed internally
- Example:
- Solution: Divide your virtual network into subnets
- Create logical segments to group similar types of resources
- Apply different rules to each subnet to control communication and improve security
Types of Subnets
| Subnet Type | Access | Use Case |
|---|---|---|
| Public Subnet | Accessible from internet | Load balancers |
| Private Subnet | Not directly accessible from internet | Databases, backend VMs, storage |
Cloud Managed Services for Virtual Networks
- AWS: VPC (Virtual Private Cloud), Subnets
- Azure: Virtual Network (VNet), Subnets
- Google Cloud: VPC Network, Subnets
What is the need for CIDR Blocks in Networking? #
Why CIDR Blocks?
- Scenario: Imagine needing to assign different ranges of IP addresses to groups of resources in a structured way — like one range for databases, another for application servers.
- CIDR Blocks: Provide a way to define and group IP addresses efficiently using a prefix (e.g.,
192.168.0.0/24), making network design easier.
What is a CIDR Block?
- Definition: Classless Inter-Domain Routing – a method to allocate IP addresses and define network sizes
- Format:
IP address/prefix length(e.g.,10.0.0.0/16) - Prefix Length: Tells how many bits are for the network (rest are for hosts)
CIDR Block Example
- 10.0.0.0/24:
- Represents IP addresses from
10.0.0.0to10.0.0.255- Network Portion: First 24 bits Fixed (10.0.0)
- Host Portion: Last 8 bits → 256 total IPs (254 usable)
- Represents IP addresses from
Common CIDR Sizes
- /16: ~65,536 IPs – good for large networks
- /24: 256 IPs – common for subnets
- /32: 1 IP – used for a single host
CIDR in Cloud Networking
- VPC CIDR: Defines the overall IP space of a Virtual Private Cloud
- Subnet CIDRs: Divide the VPC CIDR into smaller ranges
Why are Gateways essential in cloud networking? #
Why Gateways in Cloud?
- Scenario: Your VM instance runs in a private network in the cloud. How does it connect to the internet or other networks securely?
- Gateways: Components that act as bridges between your cloud network and external networks like the internet, other cloud networks, or on-premises data centers.
What is a Gateway?
- Definition: A gateway connects different networks and manages the flow of traffic between them
- Goal: Enable communication while maintaining control and security
Internet Gateway
- Purpose: Enables resources inside your cloud network to communicate with the public internet. Without an internet gateway, virtual machines or load balancers in a public subnet can't be reached from the outside world.
- How it Works: When attached to a virtual network, the internet gateway handles both incoming and outgoing traffic for resources that have public IP addresses
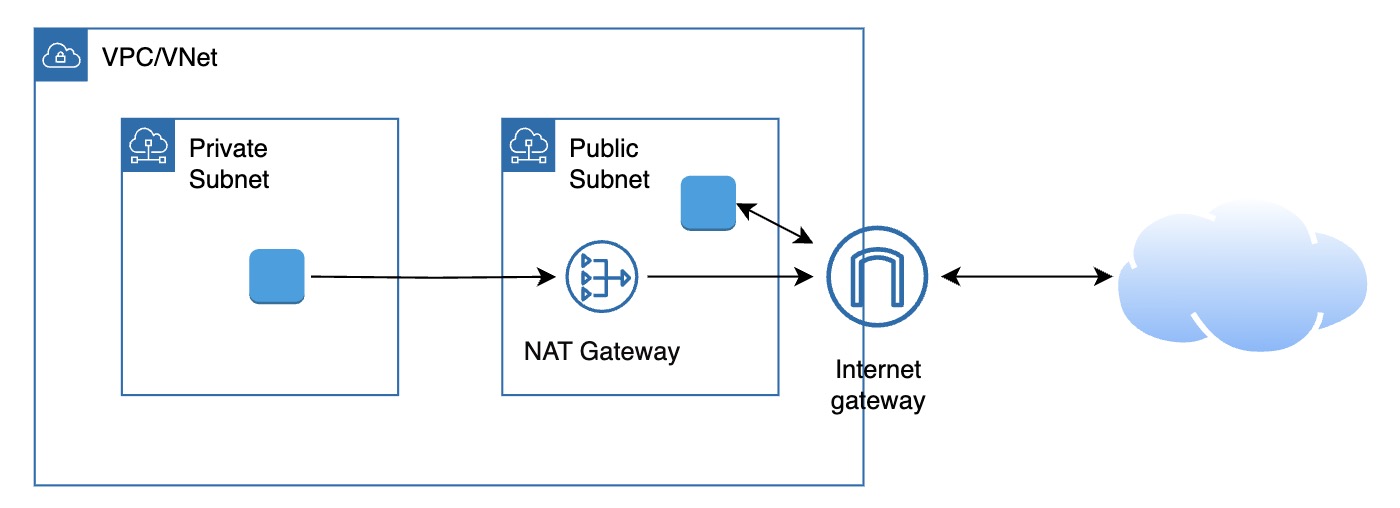
NAT Gateway
- Purpose: Allows resources inside private subnets to initiate outbound connections to the internet, such as downloading patches or calling external APIs, without being directly accessible from the internet.
- How it Works: NAT (Network Address Translation) rewrites internal IP addresses to a public IP on outbound traffic. The NAT gateway handles return traffic and blocks inbound connections.
- One-Way Traffic: Only outbound communication is allowed from the private subnet — the internet cannot initiate connections back.
- Use Case: Private VMs needing access to package repositories, external APIs, or software updates without being exposed publicly.
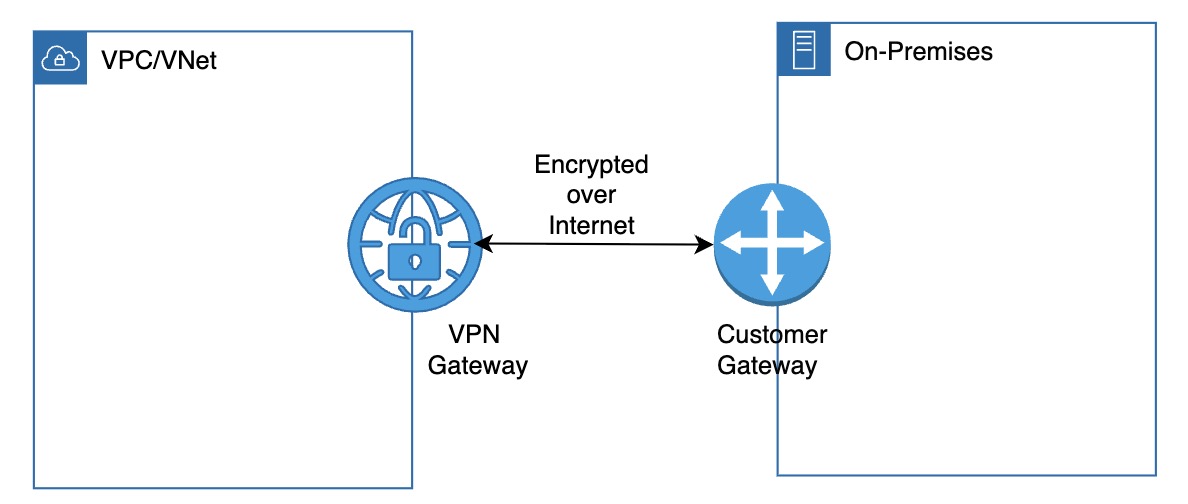
VPN Gateway
- Purpose: Creates a secure, encrypted tunnel between your cloud network and an on-premises environment or another cloud network over the public internet.
- How it Works: A VPN gateway is paired with a customer gateway. Together, they establish a secure connection that allows both networks to communicate as if they were on the same private network.
- Use Case: Hybrid cloud setup — securely extending your on-premises infrastructure into the cloud to support cloud migrations, backups, or shared applications.
What purpose do Instance-Level and Network-Level Firewalls serve? #
Why Firewalls in Cloud?
- Scenario: Imagine deploying an application without any protection. Anyone can access any port. Security risks are high.
- Firewalls: Help control who can access your resources and what kind of traffic is allowed.
What is a Firewall?
- Definition: A set of rules that allow or deny network traffic
- Goal: Protect applications by filtering traffic based on IP, port, or protocol

Instance-Level Firewalls
- Attached to a Resource: Applied directly to virtual machines or containers
- Control Inbound & Outbound: Define what traffic can reach or leave an instance
- Example Rules:
- Allow SSH (port 22) only from your office IP
- Allow HTTP (port 80) from anywhere
Network-Level Firewalls
- Applied at Subnet or VPC Level: Control traffic for all resources in a section of the network
- Example Rules:
- Block all incoming traffic by default
- Allow internal traffic between subnets
Key Differences
- Instance-Level: Granular control, applied to specific resources
- Network-Level: Broader control, applied to entire segments of your network
- Both Can Work Together: Use layered security for better protection
What is the need for Hybrid Networks? #
Why Hybrid Networks?
- Scenario: Imagine a company that wants to use the cloud for scalability but still runs critical apps on-premises. They need both to talk securely and reliably.
- Hybrid Network: Connects on-premises infrastructure with cloud resources — so both can work together seamlessly.

What is a Hybrid Network?
- Definition: A network setup that securely connects on-premises data centers with cloud environments
- Goal: Extend your private network to the cloud without exposing everything to the internet
- Use Cases:
- Gradual cloud migration
- Data residency or compliance requirements
- Low-latency access to on-prem systems
- Disaster recovery and backup
Key Options
- VPN (Virtual Private Network):
- Encrypted connection over the internet
- Cost-effective but may have limited bandwidth
- Dedicated Private Network (Interconnect/ExpressRoute/Direct Connect):
- Private, high-bandwidth, low-latency link
- Best for high-volume data transfer
Why do you need DNS service in Cloud? #
Why DNS in Cloud?
- Scenario: Imagine accessing a website using an IP address like
192.168.1.5. Not easy to remember. What if the IP changes? - DNS: Converts friendly names (like
myapp.com) to IP addresses, so users and systems can connect easily.
What is DNS?
- Definition: Domain Name System – a phonebook for the internet
- Goal: Translate human-friendly names into machine-friendly IPs
- Example:
app.mycompany.com→35.220.45.123
How DNS Works
- Step 1: User types a name like
myapp.com - Step 2: DNS finds the matching IP address
- Step 3: Traffic is sent to that IP address
DNS in the Cloud
- Fully Managed: Cloud handles scaling, reliability, and speed
- Globally Distributed: DNS servers are close to users – low latency
Use Cases in Cloud
- Access Services: Map domain names to load balancers, servers, or APIs
- Internal DNS: Name resources inside your cloud network (e.g.,
db.internal)
Advanced DNS Features
- Routing Policies: Send users to the nearest server (geo-routing)
- Health Checks: Automatically remove unhealthy endpoints
- Failover: Redirect to a backup if primary fails
Networking Components/Services Across Cloud Platforms #
| Component | Purpose | AWS | Azure | Google Cloud |
|---|---|---|---|---|
| Virtual Network | Create isolated cloud networks | VPC | Virtual Network (VNet) | VPC |
| Subnets | Divide virtual networks by access level | Subnets | Subnets | Subnets |
| CIDR Blocks | Allocate and organize IP ranges | CIDR for VPC and subnets | CIDR for VNets and subnets | CIDR for VPC and subnets |
| Internet Gateway | Allow public internet access for resources with public IPs | Internet Gateway | Internet Gateway (via NSG + LB) | Internet Gateway |
| NAT Gateway | Allow private resources to access internet without inbound exposure | NAT Gateway | NAT Gateway | Cloud NAT |
| Firewalls – Instance | Apply security rules at individual resource level | Security Groups | NSG (Network Security Group) | Instance-level Firewall Tags (targeting mechanism for VPC Firewall Rules) |
| Firewalls – Network | Apply security rules at subnet or network level | NACLs | NSG (per subnet) | VPC Firewall Rules |
| Hybrid Networking | Connect cloud with on-prem systems | Direct Connect, VPN | ExpressRoute, VPN | Dedicated Interconnect, VPN |
| DNS Service | Map domain names to cloud services and endpoints | Route 53 | Azure DNS | Cloud DNS |
| VPC Peering | Connect two virtual networks privately without using gateways | VPC Peering | VNet Peering | VPC Network Peering |
| Private Link / Endpoints | Privately connect to managed services without using public IPs | PrivateLink | PrivateLink | Private Service Connect |
| Network Monitoring & Logs | Track traffic, debug performance, and ensure compliance | VPC Flow Logs | NSG Flow Logs | VPC Flow Logs |
| IPv6 Support | Enable IPv6 addressing in virtual networks | IPv6 in VPC | IPv6 in VNet | IPv6 in VPC |